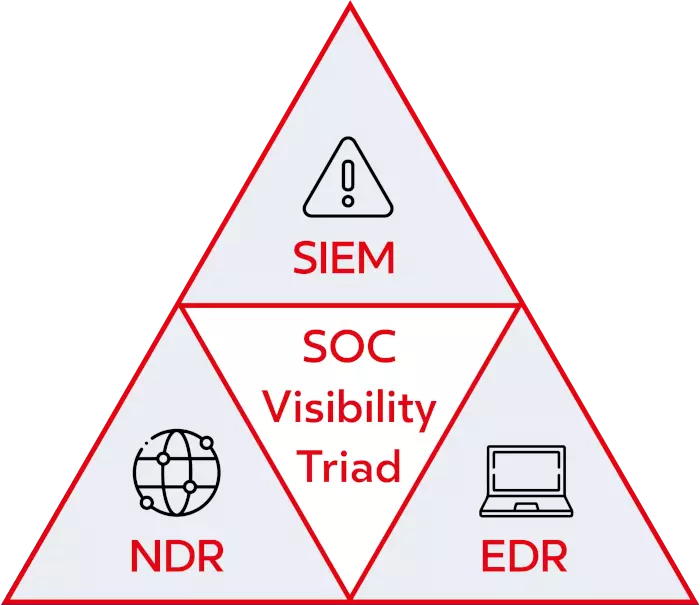
Why should you use network data for threat detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
Soc Visibility Triad Gartner . Why should you use network data for threat detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response?
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response? Why should you use network data for threat detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
Why Should You Use Network Data For Threat Detection And Response?
Soc visibility triad gartner . Why should you use network data for threat detection and response? How are networking tools used for detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
Soc Visibility Triad Gartner
Security’s Role in Client to Cloud Networking
Source: blogs.arista.com
How are networking tools used for detection and response? Why should you use network data for threat detection and response? How are networking tools used for detection and response?
NDR Network Detection and Response Hunting for Log4j using NDR
Source: www.nixu.com
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response?
Hybrid SIEM service Maple Networks work smarter and do more
Source: www.maplenetworks.co.uk
How are networking tools used for detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response?
SOC Visibility Triad Die Ultimative Abwehrlösung
Source: www.logpoint.com
Why should you use network data for threat detection and response? How are networking tools used for detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
Using Network Traffic Analysis for Detection and Response
Source: blog.rapid7.com
Why should you use network data for threat detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. Why should you use network data for threat detection and response?
From Prevention to Detection NDR and the SOC Visibility Triad CDWG
Source: www.cdwg.com
Why should you use network data for threat detection and response? How are networking tools used for detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
The SOC Visibility Triad A Vital Defense Against Cyber Threats
Source: breachpoint.com
Why should you use network data for threat detection and response? How are networking tools used for detection and response? Why should you use network data for threat detection and response?
The Role of Network Detection and Response in the SOC Visibility Triad
Source: wirexsystems.com
How are networking tools used for detection and response? Why should you use network data for threat detection and response? How are networking tools used for detection and response?
Moving from Prevention to Detection with the SOC Visibility Triad by
Source: www.vectra.ai
How are networking tools used for detection and response? Why should you use network data for threat detection and response? How are networking tools used for detection and response?
The Role of Network Detection and Response in the SOC Visibility Triad
Source: wirexsystems.com
Why should you use network data for threat detection and response? Why should you use network data for threat detection and response? How are networking tools used for detection and response?
What Traffic Mirroring Means for Cloud Security ExtraHop
Source: www.extrahop.com
How are networking tools used for detection and response? Why should you use network data for threat detection and response? How are networking tools used for detection and response?
Using MDR costeffectively against cyberattacks
Source: www.cegeka.com
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response? Why should you use network data for threat detection and response?
What is the SOC Visibility Triad? Wizard Cyber
Source: wizardcyber.com
Why should you use network data for threat detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. Why should you use network data for threat detection and response?
Lumifi Acquires Netsurion
Source: secure.lumificyber.com
Why should you use network data for threat detection and response? Why should you use network data for threat detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
The role of NDR solutions and SOC Visibility Triad
Source: exeon.com
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response? Why should you use network data for threat detection and response?
The SOC Visibility Triad
Source: www.brighttalk.com
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response? Why should you use network data for threat detection and response?
EDR and NDR efficient protection of IT infrastructure against current
Source: stinet.pl
Why should you use network data for threat detection and response? How are networking tools used for detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad.
Our partnership with Corelight delivers cost effective NDR
Source: 4datasolutions.com
How are networking tools used for detection and response? G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response?
Wat is de SOC visibility triad? Nomios Nederland
Source: www.nomios.nl
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. Why should you use network data for threat detection and response?
SOC Visibility Triad Dutch Technology eXperts
Source: dtx.nl
G00373460), augusto barros, anton chuvakin, and anna belak introduced the concept of the soc visibility triad. How are networking tools used for detection and response? Why should you use network data for threat detection and response?